Admin Application Login
The admin app for a TD site can be accessed at a URL like
https://{site-hostname}/admin (where {site-hostname} is the
fully-qualified domain name of the site.
Admin user accounts are identified by an email address. User accounts are created and maintained by a TD Security Administrator.
When accessing the TD admin application, the user is challenged for E-Mail Address
and
Password: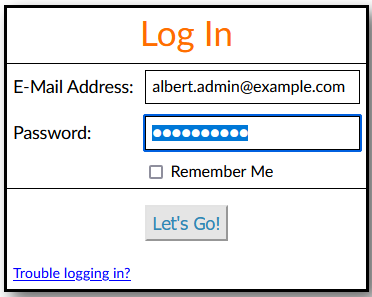 If
the credentials are valid, the application will display the user's list of Organizations.
If
the credentials are valid, the application will display the user's list of Organizations.
If the login is unsuccessful, the user will be asked to try again. After 5 unsuccessful attempts, the user account will be locked, and a TD Security Administrator must unlock it. (The maximum number of unsuccessful attempts before locking can be changed at customer request, by submitting an Oberon Support request.)
If the user has forgotten their password, the "Trouble logging in?" link will display
a dialog
for resetting the passord or resending new account notice (if user has not previously
logged
in).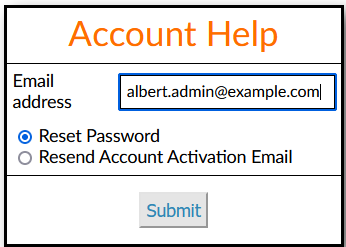
Multi-Factor Authentication (MFA)
Contact Oberon Support to request enabling MFA for admin login. You can also specify the validity time period for the security code (default 10 minutes) and the number of unsuccessful attempts allowed (default 5).
If this feature is enabled, the system will send a one-time unique security code by
email to
the user after the account id and password have been verified. The user must then
enter this
code in the dialog box: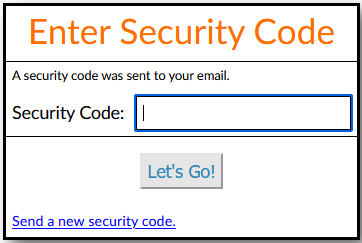 After the maximum number of unsuccessful attempts to enter a security
code, the user will be returned to the admin app login screen.
After the maximum number of unsuccessful attempts to enter a security
code, the user will be returned to the admin app login screen.
Each security code is valid for a limited time period as stated in the email. The user may request a new security code by clicking the link, "Send a new security code".
Admin Application Session Timeout
The default session timeout is 15 minutes. If there is no browser activity or communication with the server in that time, the session will expire, and the user will be prompted for login credentials.
Site administrators can request Oberon Support to modify the timeout value. Note that longer timeout values may increase security vulnerability. Administrators should check with their corporate security officer to verify compliance before requesting any change.