1 Portal Security Configuration
1.1 Configuring OIDC Authentication Clients
OpenID Connect (OIDC) is a distributed authentication framework built on the OAuth2 authentication framework. OIDC and OAuth2 are large specifications covering a wide variety of use cases for authorization and authentication. It is beyond the scope of this document to provide a complete explanation of OIDC. See the external resources below for references to applicable specifications.
A simple, typical OIDC authentication process follows these steps.
- An end user requests access to a protected resource on a website that has been configured as an OIDC Relying Party (or OIDC client).
- The website redirects the end user's browser to an OIDC provider that has been configured to authenticate requests for the requested resource.
- The OIDC provider validates the user's authorization status (possibly by requiring login).
- The OIDC provider responds to the browser with an authorization grant.
- The end user's browser sends the authorization grant to the website (relying party).
- The website validates the authorization grant and returns the protected resource that was originally requested by the user.
Many variations of this process are possible, as described in the OIDC specifications, but they all require prior configuration of OIDC Providers and OIDC Relying Parties. This process is known as "client registration", and results in an OIDC provider and OIDC relying party that can communicate throughout any supported authentication scenario.
These OIDC specifications are implemented in the Titania Delivery OIDC authentication framework.
1.1.1 OIDC Provider Requirements
Titania Delivery can be configured as an OIDC relying party (client) for most OIDC providers that conform to the relevant parts of the OIDC specifications. This topic describes special requirements and known limitations for setting up OIDC provider applications.
Refer to your OIDC provider's documentation for instructions on how to set up a new client application for your Titania Delivery site.
- Microsoft Azure AD
- Salesforce
- Microsoft ADFS
-
The OIDC provider must comply with
Authorization Codeflow as described in Section 2.1.5.1 End-User Grants Authorization and RFC 6749. -
The issuer URL is key to all OIDC authentication processes, both for locating required resources and for validating message content. In particular, for a given
{issuer-url}:- The provider must return a JSON metadata file from an HTTP request
to the well-known endpoint at
{issuer-url}/.well-known/openid-configuration. This file contains data needed to configure an OIDC relying party (client) to authenticate a user with the OIDC provider. - The provider metadata file must include an
issuerproperty with a value that exactly matches{issuer-url}.Note: Some OIDC providers support non-OIDC-compliant applications by allowing non-matching issuer URLs in the provider metadata. Titania Delivery OIDC clients cannot be configured for providers that do not comply with this requirement. - If OIDC bearer tokens from this
provider are going to be used, the
issproperty in the token must match{issuer-url}.
- The provider must return a JSON metadata file from an HTTP request
to the well-known endpoint at
-
The OIDC application redirect URI list must include a URI like:
https://[hostname]/login/oauth2/codewhere [hostname] is your Titania Delivery server platform.Note: OIDC providers use various names for the redirection URI, such as “Callback URLs” or “Authorized redirect URIs”. -
The OIDC provider must support the “openid” scope and either the “email” or the “upn” scopes.
Note: This may require modifying the default configuration when setting up a client application.
After the OIDC provider client application is configured, the TD administrator will need the issuer URL, client id, client secret, and any custom scopes required by the provider in order to complete the client registration process in Titania Delivery.
1.1.2 Configuring OIDC Security Profiles
The OIDC provider must have previously been configured (see OIDC Provider Requirements), and the TD administrator must have the following information from the customer's OIDC provider to start the configuration process.
-
The issuer URL of the OIDC provider. (See Section 2 of the OpenID Connect 1.0 specification and your OpenID provider documentation.)
-
The
Client Idthat is generated by the authorization provider when a client application is created by your OIDC system administrator.Note: Some providers allowClient Idvalues to be user-generated. -
The
Client Secret, which is also generated by the provider when the client application is created. -
Any custom scopes required by the OIDC provider.
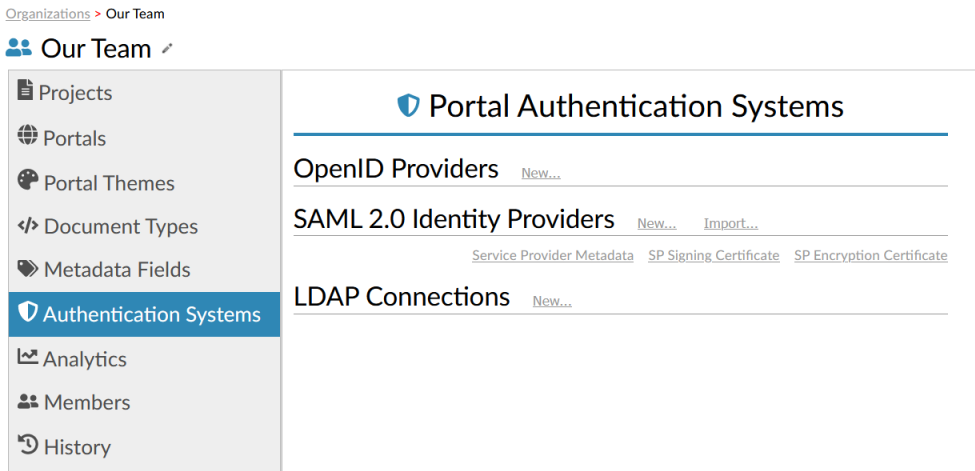
- Go to, or create, a Titania Delivery Organization to add a new authentication system.
- Click Authentication Systems.
-
In the Portal Authentication Systems page, click New in the OpenID
Providers section.
The OpenID Provider window will appear.
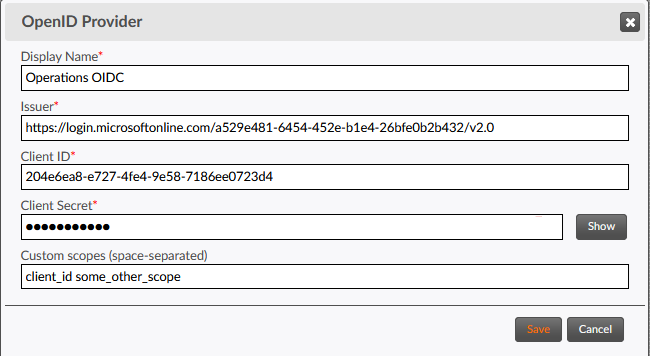
- In the Display Name field, enter a label for the OpenID provider. This label should be unique among all OpenID profiles on your TD platform, to avoid ambiguity when selecting a security profile for a portal.
- In the Issuer field, enter the issuer URL of your OIDC provider application.
-
In the Client ID field, enter the
Client Idcreated or generated when the client application was created by your OpenID system administrator. -
In the Client Secret field, enter
the
Client Secretgenerated when the client application was created by your OpenID system administrator. - If your OIDC provider requires custom scopes to process an authorization request, enter them in the Custom scopes field, separated by spaces. Otherwise, leave this field blank. If present, custom scopes will be appended to the default scopes used for the OIDC protocol.
- Click the Save button.
1.2 Configuring SAML Security Profiles
Overview
The high-level steps to set up a TD security configuration for a SAML IdP are:
- (Titania Administrator) Export the Titania Delivery SAML Service Provider metadata as an XML file. This is the "SP metadata".
- (SAML Administrator) Register Titania Delivery with the chosen SAML IdP, using the information in the SP metadata, and additional requirements as specified in SAML Identity Provider SSO Configuration.
- (SAML Administrator) Export the "federated metadata" from the IdP, or provide the
URL for the
federated metadata.
Note: Alternatively, the required information can be entered manually in the TD security configuration form. See Manual SAML Security Configuration.
- (Titania Administrator) Set up the SAML security profile in Titania Delivery, either manually, or by importing the federated metadata.
- (Titania Administrator) As needed, associate the SAML security configuration with portal(s) that will use this IdP for authentication. See Portal Security
SP Metadata and certificates
The admin page provides persistent links to the following SAML resources, under the SAML 2.0 Identity Providers heading:
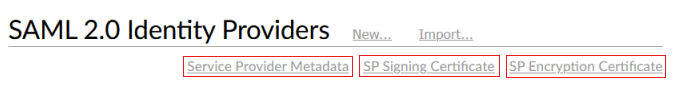
- Service Provider Metadata
- The Entity Descriptor (SP metadata) XML for Titania Delivery, for use in configuring IdPs to accept authentication requests from Titania Delivery. The URL for this metadata is persistent for the Titania Delivery platform, and can be registered with IdP services that support automatic metadata refresh.
- SP Signing Certificate
- The certificate corresponding to the key that will be used by Titania Delivery when signing authentication requests.
- SP Encryption Certificate
- The certificate that must be used by Identity Providers when encrypting authentication responses being sent to Titania Delivery.
Entity ID and IdP-Initiated SSO
If you plan to use IdP-initiated SSO (as described in SAML V2.0 Technical Overview, Section 5.1.1), you should configure your SAML identity provider to send SAML SSO <Response> messages with a form control or URL query parameter named RelayState whose value is the fully-qualified URL of the requested portal. Otherwise, if there are multiple SAML IdP Configurations with the same Entity ID on the TD platform (across all organizations), Titania Delivery may fail to fulfill the request. If the RelayState parameter is not provided, then Titania Delivery will not display a portal page.
If you create SAML IdP Configurations with duplicate Entity IDs, and do not use IdP-initiated SSO, this will not be a problem. Duplicate Entity IDs will typically be created automatically when importing IdP federated metadata from the same provider.
Additional SAML user assertions
SAML IdPs may be configured to include additional assertions (properties) about the user with a successful authentication response. These properties are stored with the portal user object, and are available for use in portal themes and for dynamic content filtering.
SAML user assertions do not need to be registered with Titania Delivery in advance.
All such
assertions in an authentication response are put into a map object, using the
SAML technical name as the key. This map is available as the user.properties
property.
Microsoft ADFS IdP requirements
From TD version 4.5.0 and on, Microsoft ADFS SAML IdP Relying Party Trusts property must be set as described below.
An ADFS administrator must use a PowerShell command to modify the
SamlResponseSignature property of any relevant Relying Party Trusts.
Use the following PowerShell command to view the property:
Get-AdfsRelyingPartyTrust -Name [Relying Party Trust Name]where [Relying Party Trust Name] is the Display Name of the trust. Search for the value of the
SamlResponseSignature property. The required value is
MessageAndAssertion.
Use the following PowerShell command to set the property:
Set-AdfsRelyingPartyTrust -Name [Relying Party Trust Name] -SamlResponseSignature MessageAndAssertionwhere [Relying Party Trust Name] is the Display Name of the trust.
1.2.1 Manual SAML Security Configuration
From the page in the TD admin application, click the New... button next to the SAML 2.0 Identity Providers heading. This dialog allows the manual configuration of the Identity Provider settings.
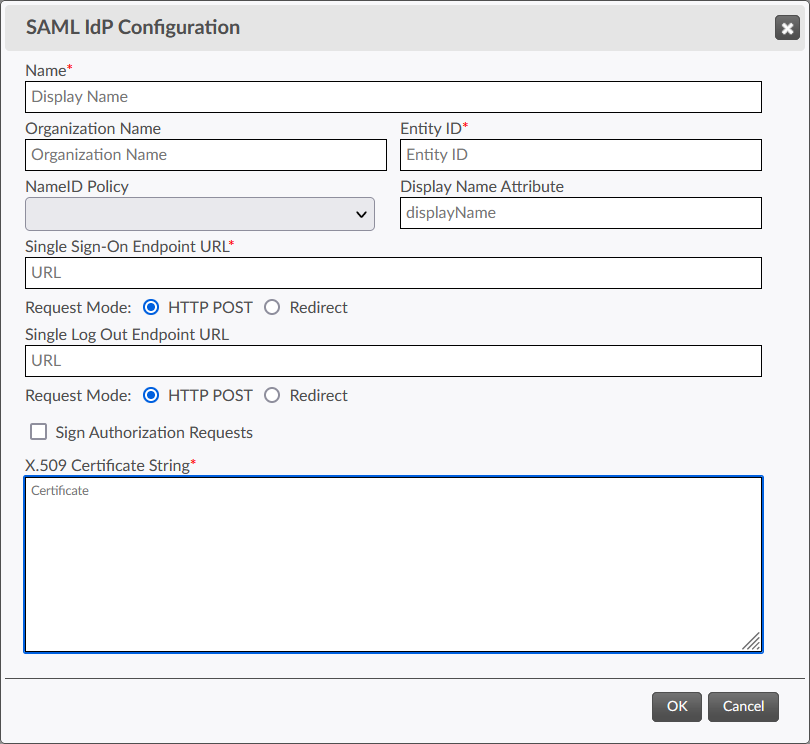
- Name
- The display name for the configuration. This is not used in the authentication process, and is simply a label for the configuration.
- Organization Name
- The Organization Name for the IdP.
- Entity ID
- The entity ID for the IdP service.
- NameID Policy
- The NameID policy to specify when making authentication requests with the IdP.
Note: Not all Identity Provider implementations honor the NameID policy specified in authentication requests. It is often the case that the NameID value must be separately configured in the Identity Provider service's configuration settings.Important: The NameID provided by the IdP is used as the persistent user ID within the portal for purposes of tracking comments made by the user, and assemblies owned by the user. SAML 2.0 allows for transient NameIDs, such that every authentication results in a different value for the same user. While this will work for authentication purposes, Titania Delivery will treat each new session as if it were a new user, and so the ability to manage assemblies and comments from previous sessions will be lost. In general, we strongly recommend using a persistent NameID value, such as e-mail address or other persistent ID.
- Display Name Attribute
- The attribute that will be included in any authorization response which corresponds to the user's display name.
- Single Sign-On (SSO) Endpoint URL
- The URL that the IdP service uses to accept authentication requests. This may be found in the federated metadata provided by the IdP, or directly from the IdP configuration.
- Request Mode (SSO)
- The mode to use when issuing authentication requests to the IdP service. It is recommended to use "HTTP POST".
- Single Log Out (SLO) Endpoint URL
- The URL that the IdP service uses to accept logout requests. This is typically the same URL as the Single Sign-On Endpoint URL. It may be found in the federated metadata provided by the IdP, or directly from the IdP configuration.
- Request Mode (SLO)
- The mode to use when issuing logout requests to the IdP service. It is recommended to use "HTTP POST".
- Sign Authorization Requests
- When checked, authorization requests sent to the IdP will be signed using the key corresponding to Titania Delivery's signing certificate. It is recommended always to sign requests, for greatest security.
- X.509 Certificate String
- The Base64-encoded string representing the certificate that will be used to verify signed values in authentication responses provided by the IdP. This value is provided in the IdP''s federated metadata, or it can be obtained directly from the IdP configuration. It is recommended to configure your IdP to sign responses, for greatest security.
1.2.2 Importing SAML IdP Settings
SAML IdP service provider settings may be exported from the IdP as a "federated metadata" XML file; alternatively, it may be retrieved from a specified URL on the IdP.
To import the federated metadata and automatically configure the TD security profile, select the page in the TD admin application, and click the Import... link next to the SAML 2.0 Identity Providers heading.
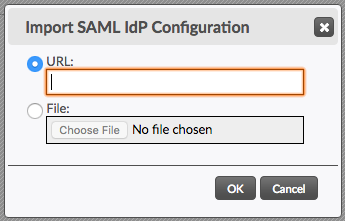
SAML federated metadata can be imported either from a public URL or by uploading the metadata file. Select the appropriate radio button and provide the URL or file. Then click OK.
displayName for this purpose if available, and
will use the provided NameID value otherwise.1.2.3 SAML Identity Provider SSO Configuration
Best practices for configuring a SAML identity provider to register Titania Delivery as a service provider.
Signing Requests and Responses
Requiring signed requests is one way the IdP can verify that requests are sent from a trusted relying party. The IdP should configured to required signed requests, and to send signed responses.
Assertion Consumer Service URL
The Assertion Consumer Service of a SAML relying party is responsible for
receiving and processing SAML responses . On the Titania Delivery platform, the assertion
consumer service is available at a URL like
https://[td-hostname]/portals/saml2/assert. The
<AssertionConsumerServiceURL> element of the TD service provider
metadata XML file contains the specific value for each TD platform. When registering
Titania
Delivery as a service provider with your IdP, the configuration will include this
URL, which is
used to route responses from the IdP to Titania Delivery.
The assertion consumer service URL provided in the SP metadata may be over-ridden
in SAML
authentication requests to the IdP. All requests originating from Titania Delivery
will include
an <AuthnRequest>/@@AssertionConsumerServiceURL attribute
with a value like https://[td-hostname]/portals/saml2/assert/[registration-id],
where [registration-id] is an arbitrary alphanumeric string. The SAML 2.0 Core specification requires IdPs to:
- Recognize URLs like this as valid assertion consumer service URLs for this service
provider. Different IdPs will have different ways of configuring this. It might be
possible to
define the valid assertion consumer service URLs using a pattern with a wildcard,
such as
https://[td-hostname]/portals/saml2/assert/*. In other IdPs, if the requests are signed, they will use the assertion consumer service URL provided in the request. - Return the authorization reponse to the URL provided in the request (including the
registration-id).
RelayState
The SAML 2.0 Bindings specification defines a "RelayState" mechanism for preserving state between SAML entities during message exchanges. The specification requires responders to faithfully include any received relay state data in their response. In HTTP POST and redirect protocols, relay state is transmitted as a URL-encoded value of a URL parameter (or form control) named "RelayState".
Authentication requests originating from Titania Delivery will include a "RelayState" URL parameter (or form control) with a value representing the secured portal URL. This value must be returned with the authorization response.
For IdP-initiated authentication, the SAML authorization response sent to the assertion consumer service must include a "RelayState" parameter with the URL-encoded value of the URL of the requested portal.
1.3 Configuring LDAP Connections
LDAP configurations are associated with Organizations. To establish an LDAP connection, select the Security category of the organization and click the New... link next to the LDAP Connections header to raise the LDAP Security Configuration dialog.
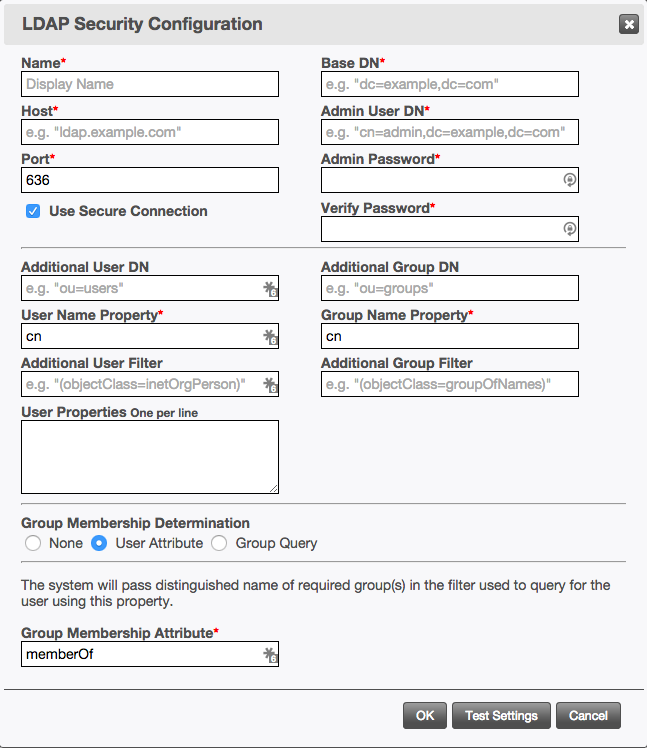
-
Name
The field names on this page do not appear in bold like in other sections. For example, see Part III.1.
- A name identifying the LDAP connection.
- Host
- The hostname or IP address of the LDAP protocol listener on the directory server.
- Port
- The port number on which to connect to the directory server.
- Use Secure Connection
- Whether to use LDAPS to communicate with the directory server.
- Base DN
- The full Distinguished Name of the node within the directory server.
- Admin User DN
- The full Distinguished Name of the account Titania Delivery will use to connect to the directory server.
- Admin Password
- The password for the account identified in the Admin User DN.
- Additional User DN
- Additional Distinguished Name segments to prepend to Base DN when querying the directory server for users.
- User Name Property
- The property in the directory system that will be used to test the user name for authentication attempts.
- Additional User Filter
- An LDAP query to append to the default query used when searching for users in addition to the User Name Property.
- User Properties
- Additional object properties from the directory server to retrieve when a user logs
in.
These properties will be made available in the
propertiescollection on the object available to all portal pages once a user logs in. - Additional Group DN
- Additional Distinguished Name segments to prepend to Base DN when querying the directory server for user groups.
- Group Name Property
- The property in the directory system that will be used as the group's name.
- Additional Group Filter
- An LDAP query to append to the default query used when fetching groups.
- Group Membership Determination
- This is the method used to determine whether a user is a member of a group.
- None
- No group membership checks will be performed, and group-based access control will be disabled.
- User Attribute
- Use this when the directory server supports a dynamic property on the user object
listing the groups to which a user belongs. For example, the
memberOfproperty in Active Directory. - Group Query
- Use this when the directory server does not support any sort of
memberOfproperty. When group-based access control is configured for a portal, Titania Delivery will first authenticate the user, and then execute a second query to verify that the user is a member of the specified group.
1.4 Portal Security
You assign a security system to a portal using the portal's Authentication tab.
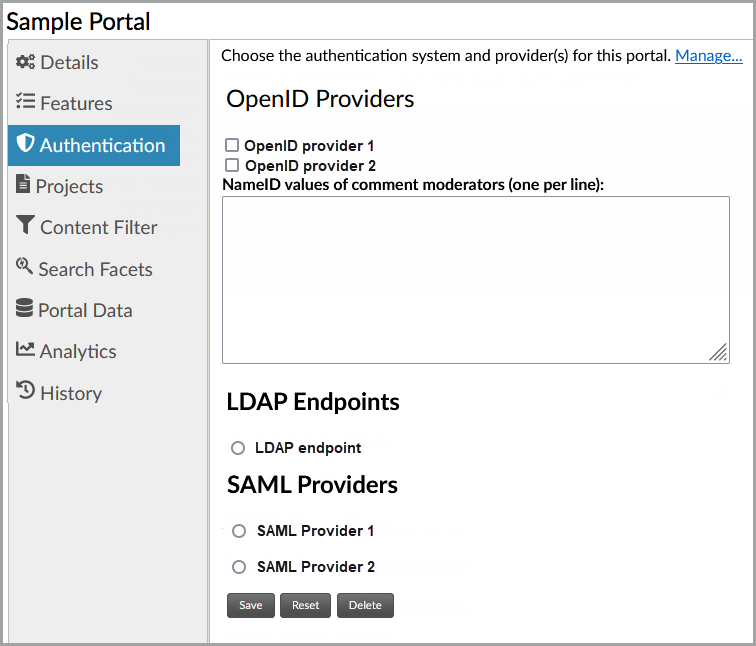
The list of available security configurations is populated by those available in the organization that owns the portal, as well as those set up in the System Administrators organization, which are global. Once the portal is associated with a security configuration, additional details can be specified.
If using an LDAP-based configuration, you can specify the lists of users and/or organizations within the repository that will have access to the portal. You can also specify which users should be granted Comment Moderator rights within the portal, meaning that they can edit, delete, and set dispositions of other users' comments.
If using an OpenID-based or SAML-based service, you can only specify the list of NameID values to be granted comment moderator rights.
If using OpenID authentication, you may select more than one OpenID provider for the
portal. The portal theme must include a template file at pages/oauth2login.ftl,
which will show the available OpenID providers from which the user may choose one.
Theme developers
may customize the style of this page. A default template is provided in the Titania Default
Theme.
To unset all security providers for the portal, click the Delete button.
After making changes, click the Save button.
The default portal theme includes a page that can be used to review
the current session's security information, including the authenticated
user, their properties, and the results of the dynamic security
script, including print() output. This page can be
included into any portal theme, though it is generally not linked
to from any of the main pages, and primarily exists as a debugging
tool. It can be found at the URL /portalUrlPath/pages/userInfo. This page can be used to view the
properties and, for SAML 2.0, NameID value for the currently logged-in
user, as well as details about the dynamic filter script output,
if any.
1.4.1 OIDC Bearer Tokens
For portals that use OpenID Connect (OIDC) authentication, portal requests can use Bearer tokens to authenticate. The OIDC provider must support token generation and validation (and optionally, refreshing tokens). The process for configuring OIDC providers for token support will vary with the provider. Consult your OIDC provider administrative documentation for details and requirements.
The OIDC client registration must support scopes "openid" and "offline_access", and conform to the OAuth2 "Authorization Code" flow. Titania Delivery only supports OIDC bearer tokens in JWT (JSON Web Token) format. The "iss" claim in the token must match the "issuer" URL in the TD OIDC security configuration (see Configuring OIDC Authentication Clients).
The OIDC security configuration must be set up in an organization accessible by the portal, and the portal must be configured to use the OIDC security configuration.
The process for using Bearer tokens is:
- A third-party application (or web page) authenticates itself with the OIDC provider.
- The client application obtains a bearer token from the OIDC provider.
- The client makes an HTTP request to a portal URL, and includes the bearer token.
The bearer token may be attached to the request in one of these ways:
- Put the bearer token in the
Authorizationrequest header, preceded by the literal string "Bearer ". (This is the most secure, and preferred, method. See "Authorization Request Header Field" section in the "OAuth 2.0 Bearer Token Usage" RFC for additional details.) - In a POST request, add the bearer token as the value of a form url-encoded parameter named "access_token" in the body of the request. (This is less secure, and should be used only when the client application is unable to set request headers. See "Form-Encoded Body Parameter" section in the "OAuth 2.0 Bearer Token Usage" RFC for additional details.)
- In a GET or POST request, add the bearer token as the value of a URL
query parameter named "access_token".
Note: This is considered a higher security risk than the other methods. By default, Titania Delivery does not support this method. Customers may request Oberon Technologies to enable this method for their site after acknowledging and accepting the security risks. (See "URI Query Parameter" section in the "OAuth 2.0 Bearer Token Usage" RFC for additional details.)
- Put the bearer token in the
- Titania Delivery will validate the token using information from the OIDC
provider. If the token is valid, the request will be processed normally. If the
token has expired, the portal will attempt to obtain a fresh token, and, if
successful, will return a 4xx HTTP response with the new token in the
WWW-Authenticateresponse header. The client application may resubmit the request with the new token, or take other action. If the token cannot be validated, a 4xx HTTP response will be returned to the client.
The following industry standard specifications provide additional details about the processes and entities described here:
1.4.2 Troubleshooting SAML Authentication
The Titania Delivery SAML authentication framework is designed to implement the preferred security recommendations available in the SAML protocol. There are a variety of SAML Identity Provider (IdP) applications available. If your SAML IdP supports the recommended security features that TD uses, it will be possible to configure TD to use your SAML IdP.
SAML Tracer
SAML protocol tracers are available as plugins or addons for various browsers. One such tool is SAML Tracer for Mozilla Firefox. Oberon Technologies make no representation or guarantees about the safety or suitability of this tool. Consult your enterprise IT security policies before installing or using any SAML tracer plugin.
A SAML tracer can display the details of the various SAML requests, responses, and redirects that occur during SAML authentication. This can help an experienced SAML administrator identify the possible causes of a SAML authentication problem.
Troubleshooting
- Review the configuration of the SAML security profile that is associated to the portal. Be aware that many security profiles with similar settings and names may have been defined on your system.
- Check the IdP configuration for the IdP to verify that the settings agree with settings in the SAML security profile, and meet the requirements described in SAML Identity Provider SSO Configuration.
- Make sure all X.509 security certificates are up to date on your SAML IdP. Instructions for checking security certificates should be available in your IdP's administration guide.
- Do the certificate strings on Titania Delivery's SAML configuration form match the expected data configured (or auto-configured) on your SAML IdP? Some IdP’s can be configured to auto-update if Titania’s “Service Provider Metadata” changes.
- Does the IdP’s X.509 certificate string match the SAML configuration on Titania Delivery?
1.5 Secure Portal Session Timeout
By default, all Titania Delivery portal sessions time out after 15 minutes of inactivity. When the portal is unsecured, or the user is browsing anonymously, a new session will automatically be created when the user navigates to a portal page after a timeout. The user will typically not notice any interruption of service.
Contact Oberon Support to request a change to the portal timeout value. Any change will apply to all portals on the site.
When the user is authenticated in a portal session that times out, the behavior may be different, depending on what authentication method is used and how the system is configured.
OpenID Connect authentication
When an OpenID-authenticated portal session expires, the system will automatically reauthenticate a new session.
SAML2 authentication
In the default deployment configuration, when a SAML-authenticated portal session times out, the system will automatically reauthenticate a new session with the SAML IdP.
The default behavior may not be desired in all cases, because it raises the risk of "tailgating" access by unauthorized users. For example, if a secure portal is available on a public computer, and one user fails to log out of the portal, another user with different privileges could subsequently gain access to the portal, even after the session has timed out.
Customers may request Titania Support to change the deployment configuration for their site, to force re-authentication after session timeouts. This change will apply to all SAML-authenticated portals on the site. Users will be challenged for login credentials every time they attempt to navigate to a portal page after the session has timed out.
LDAP authentication
When an LDAP-authenticated portal session expires, the user will be challenged to re-enter credentials when navigating to a new portal page or refreshing the current page.
1.6 Dynamic Content Filtering
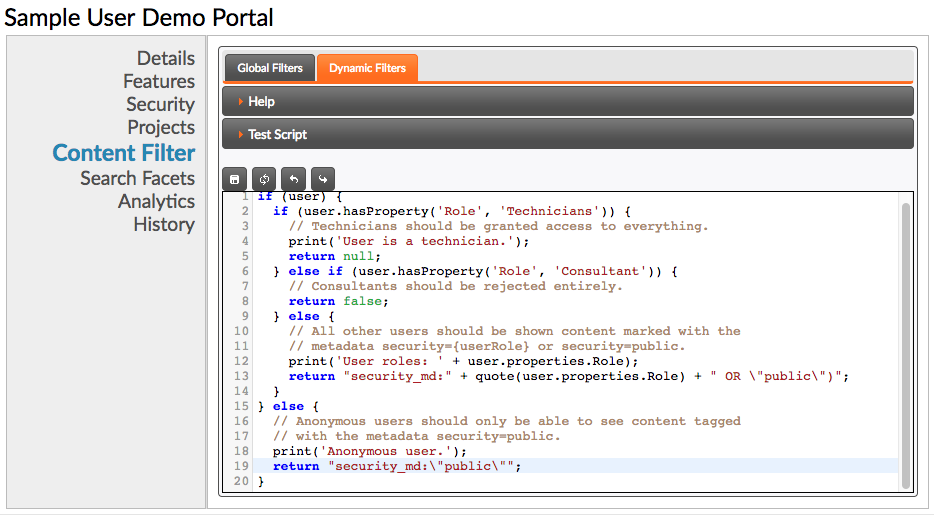
The script will be given a user variable containing the identity of the
authenticated user, if any. If there is no user, it will be null. The script
should end with a return statement returning one of the following.
- A string containing a search query for content access filtering. This query will be included in all content queries during the user's session. The user will only be able to see content that matches the given filter query.
-
false, in which case the user will be prevented from accessing the portal entirely. -
nullorundefined(or noreturnstatement at all), which will result in no additional filtering being applied.
Interrogating the User's Properties
The identity provider may provide additional properties associated with the authenticated user. This script can access those properties to make decisions about what content the user can access using the following properties of the user object.
-
Map properties - The user properties pulled from the authentication service. For SAML-secured and OpenID-secured portals, this will contain whatever attributes were included in the authentication response message sent by the Identity Provider. For LDAP-secured portals, this will contain the properties listed in the LDAP connection configuration. NOTE: This collection allows for multi-valued properties, so values are arrays, not single values. Properties with single values will be lists of size 1.
-
boolean hasProperty( String name, String value) - Tests whether there exists a property with the given name containing the given value. If the value is not specified, this method tests whether the property exists.
The script also provides the following utility functions.
-
escape(str) - Escapes reserved characters in the given string so that it can be used inside a search string.
-
quote(str) - Like
escape(), but additionally wraps the text in quotes. -
print(str) - A degugging function that prints the given string to the execution log. See below for how to read the log output.
The provided script will be executed at the following times.
- If the portal supports anonymous access, the script will be run when a user first
accesses
the portal, with a
nullvalue for user. - Immediately after a user authenticates with the portal, with the user populated with the username and properties provided by the identity provider.
- If the portal supports anonymous access, the script will also be run after an authenticated
user logs out, again with
nullfor user.
Script Testing
Once the script is entered, it can be tested using the Test Script section of the page, which allows you to construct a user and their properties to run through your filter function.
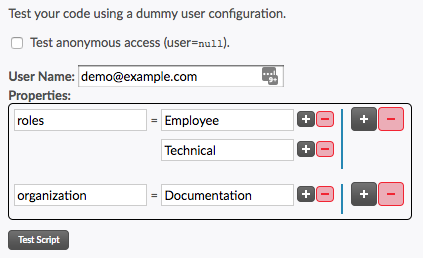
- Specify whether or not an anonymous user will be used.
- Specify the username and properties for the dummy user, if desired.
Note: User properties are multi-valued. The provided interface allows you to add multiple values for properties (smaller buttons), as well as adding and removing additional properties (larger buttons).
- Click the Test Script button.
The script will be executed on the server, and the results of the script will be printed
below
the form, including strings passed to the print() function.
The /pages/userInfo page in the default portal theme can also be used to
view the script output for the currently-authenticated user in a live portal.